Identifying a cyber security risk isn’t always easy, even for experts. Assessing cyber risk in the marine industry can be even harder. Fortunately, a number of industry bodies, including BIMCO, CLIA, ICS, Intercargo and Intertanko, have joined together to publish guidelines to assist shipping companies with their cyber security efforts.
The guidelines, discussed further below, are available from:
Risk assessment – familiar territory
The guidelines assess risk and lead to putting measures in place to control that risk, a familiar process for shipping companies. The image below, taken from the guidelines, shows the process. Below we briefly each step.
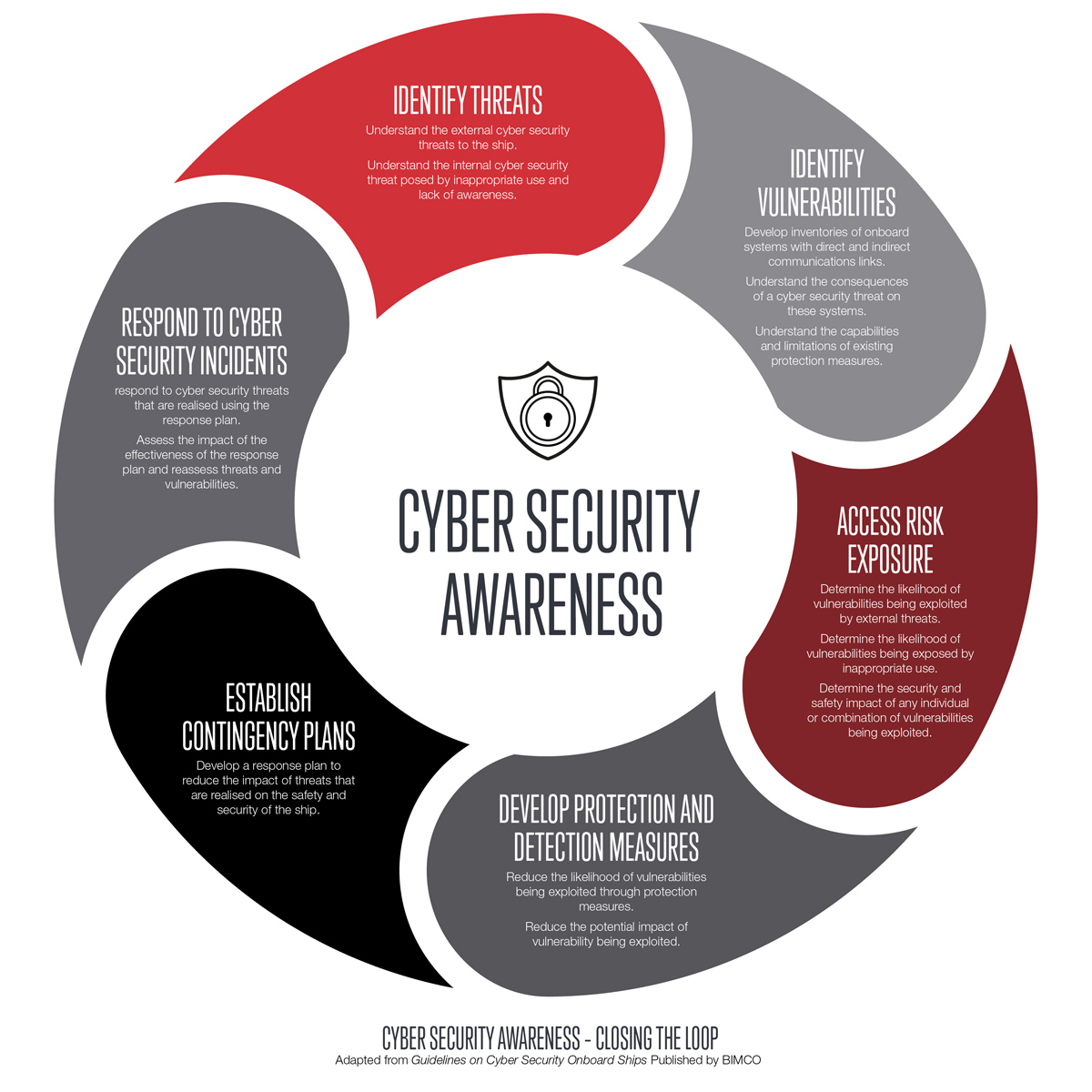
Who might be a threat to you?
The BIMCO guidelines identify four groups who may give rise to a threat. From there you consider the risk posed to your company by the different groups. For example, a container operator is probably at more risk from criminal gangs seeking to steal cargo than a bulk cargo operator because more of the goods carried in the container trade are easily portable and have a high value.
Group |
Motivation |
Objective |
|
|
|
|
|
|
|
|
|
|
|
|
How might they attack?
Companies are at risk of attack, both targeted and untargeted, in much the same way as individuals are. Attacks may come in all sorts of forms: you may already have heard terms like phishing, spear phishing, botnet and water holing. These are explained in the guidelines as are the stages of a cyber-attack. The key message is that personnel should aware of these potential cyber security risks and be trained to identify them and to mitigate the risk.
What are the risks?
It is important that you think about how cyber security might affect business practices, internal relationships and customer relationships. The guidelines suggest using the five-part cyber security framework described by the National Institute of Standards and Technology (NIST) Cyber Security Framework: Identify, Protect, Detect, Respond, Recover.
An initial risk assessment should identify:
- Which IT systems and operational technology systems are vulnerable and how they are vulnerable.
- What controls are in place to protect the systems and whether these cover the vulnerabilities.
- Which key shipboard operations are vulnerable.
- The identification of possible cyber incidents, their impact on shipboard operations and their likelihood.
All of this will take time and resource. It may therefore be more cost-effective to use third parties to assist in identifying them. Ideally, such a company would have both IT security expertise and experience in shipping. This is something North can help with; see our Member Benefit – Cyber Security Evaluation.
The assessment should produce a report that identifies the vulnerabilities and assesses the risks posed by them in terms of impact and probability. From this, decisions can be taken on corrective actions that will reduce risk.
Reducing risk
In general there will be two types of response; technical responses (dealing with equipment and systems); and procedural responses (focussing on how systems are used and how humans interact with them).
Technical responses can deliver quick wins, while getting procedural controls in place requires changing existing practices and attitudes, involves awareness raising and training and can take time.
Plan for the worst!
It is almost inevitable that your company or vessel systems will be compromised by a cyber threat at some point, if this has not already occurred, so you should have contingency plans in place to deal with the threats and the impacts they might have.
The guidelines set out some of the critical elements related to ships for which plans should be made:
- What should you do if electronic navigational equipment is disabled or manipulated?
- What should you do if industrial control systems for propulsion, auxiliary systems and other critical systems are disabled or manipulated?
- How can you verify that data is intact where penetration is suspected but not confirmed?
- How do you respond to ransomware incidents?
- How do you respond where land-based data is lost?
Respond, Recover, Investigate
Respond: identify what’s happened or is happening and take action to address the incident. This may mean shutting down systems or communications links, de-activating software and involving persons from either your own IT department or even external IT expertise.
Recover: reinstatement of essential ship or system functions may need shore-side assistance. How and where to get assistance (for example by proceeding to a port or contacting a particular supplier) should be set out in the recovery plan.
Investigate: working out what happened and how it happened should result in a better understanding of the threats you and your ships are facing, lessons to be learned and any updates that are required to technical and procedural controls.
Investigating cyber incidents can be a complex and challenging task: external expert assistance might be the best option.

 , you have now set your site language to English. If you'd like to change your language preference again, simply click on one of the other flags.
, you have now set your site language to English. If you'd like to change your language preference again, simply click on one of the other flags. を選択して頂くと、言語設定が日本語に切り替わります。設定変更後は以下の機能が利用可能です。
を選択して頂くと、言語設定が日本語に切り替わります。設定変更後は以下の機能が利用可能です。
 ,可将网站语言设置为中文。这能帮助您:
,可将网站语言设置为中文。这能帮助您:



